Understanding Extraterritorial Overreach: Navigating Global Sanctions, Tech Stacks, and Data Governance Risks in 2025
When sovereignty gets coded into infrastructure, compliance doesn’t stop at the border.
Foreword
As of April 2025, the rules of global business are no longer just written by national regulators—they're enforced across borders through infrastructure, finance, and code.
The United States, long dominant in extraterritorial law enforcement, has inspired imitators: China, the EU, Russia, the UK, and Canada now deploy legal, economic, and digital levers to pressure foreign companies for political, security, or moral reasons—even when those companies have no direct legal presence in their jurisdictions.
For executives, CISOs, CIOs, CTOs, and Risk Officers at multinational corporations, these developments are reshaping everything from supply chain design to cloud architecture to data governance.
This article explores the mechanisms of extraterritorial overreach using ten global case studies. Each highlights a different lever of enforcement, impact on tech stack or data, and critical lessons for corporate strategy and risk mitigation.
Introduction: The Hidden Costs of Dollar Dominance
The U.S. dollar doesn’t just buy goods — it enforces rules, shapes global trade policy, and carries legal jurisdiction beyond borders. For business leaders, especially CIOs, CTOs, CDOs, and CFOs, this is no longer just a financial consideration — it’s a risk factor embedded in your tech stack and operating model.
This article dissects:
How U.S. trade imbalances are misunderstood
Why the dollar enables legal and regulatory overreach
What real-world cases illustrate the risk
How business and technology leaders can mitigate exposure
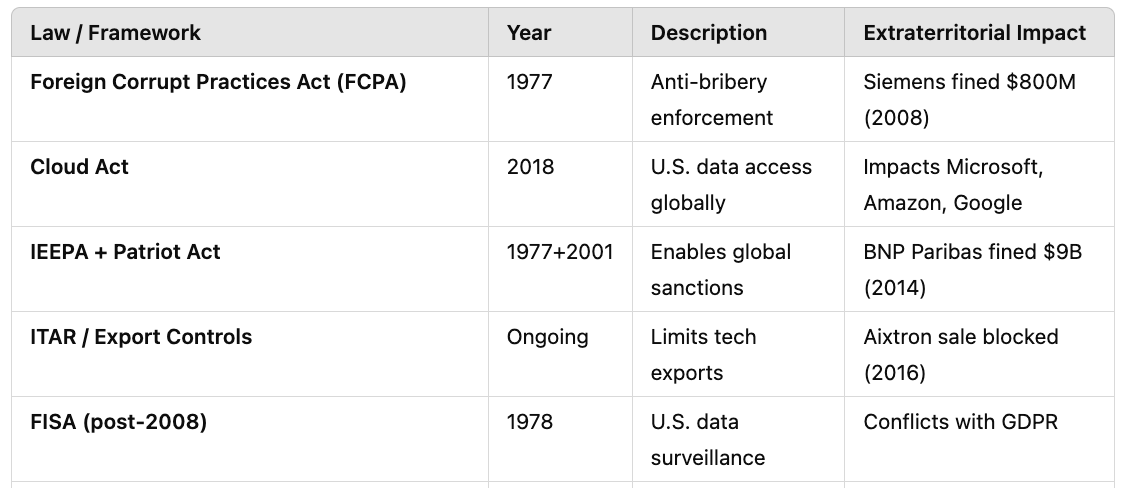
Key Concept: “Extraterritoriality of the U.S. dollar” refers to the ability of U.S. authorities to enforce American laws and policies on non-U.S. entities engaging in dollar-denominated transactions or using U.S. financial systems.
It works because the U.S. dollar remains the world’s primary reserve currency, accounting for roughly 60% of foreign exchange reserves as of 2021 (The Fed) - although it fell down to 57.4% in Q3 2024, which is the smallest share since 1994 and a decrease of almost 9% over the past decade.
U.S. Trade Deficit? Not So Simple
The U.S. ran a goods trade deficit of over $1 trillion in 2023, which has fueled populist narratives of exploitation. But this ignores the $300 billion surplus in services, and the massive global export of digital goods and intellectual property.
In 2023, IP royalties alone brought in $146 billion.
(Sources: bea.gov, commerce.gov)
This surplus is driven by software, streaming, cloud services, and professional services — exported from the U.S. but consumed globally. The 'deficit' narrative fails to account for this asymmetric digital dominance.
It’s more a reflection of the state of the US economy in the 21st century (focused on services and digital products, innovation and intellectual property) rather than industrial manufacturing of goods (a 20th century economy).
Dollar Dominance = Regulatory Control
With ~59% of the world’s foreign exchange reserves in USD (IMF COFER), the U.S. dollar remains the default medium for global trade and financial settlement. But that privilege brings:
The ability to unilaterally impose sanctions
Extraterritorial export control enforcement
The power to force compliance with U.S. regulations — even for non-U.S. entities
The Mechanisms of Enforcement are listed below.
They enable U.S. regulators to penalize non-U.S. firms if their actions involve dollars, U.S. banks, or U.S.-based infrastructure — even if they never set foot in the U.S.
(Sources: Theoria Vol. 68 (2021), Clarip, International Bar Association, White & Case LLP)
This is not just theoretical.
Below are detailed case studies illustrating how U.S. law reaches beyond its borders, as well as similar tactics increasingly used by China, the EU, and others.
But these benefits come with growing global resistance.
China’s Yuan settlement agreements, the Digital Euro initiative, and BRICS-led de-dollarization efforts threaten to weaken U.S. leverage.
Sources:
Brookings on China’s BRI
Real-World Case Studies of Extraterritorial Reach
In this article we examine 10 case studies of extraterritorial overreach, split between US and non-US examples, to provide a balanced perspective.
Each case details the lever used, the method of enforcement, the impact on the targeted entity, and lessons for prevention and preparedness.
Drawing from authoritative sources, we aim to equip leaders with actionable insights to safeguard their organizations amid escalating geopolitical tensions.
Part 1: US Extraterritorial Overreach
The US has wielded its economic and legal might to influence foreign companies, often citing national security, anti-corruption, or sanctions compliance. Below are five illustrative cases.
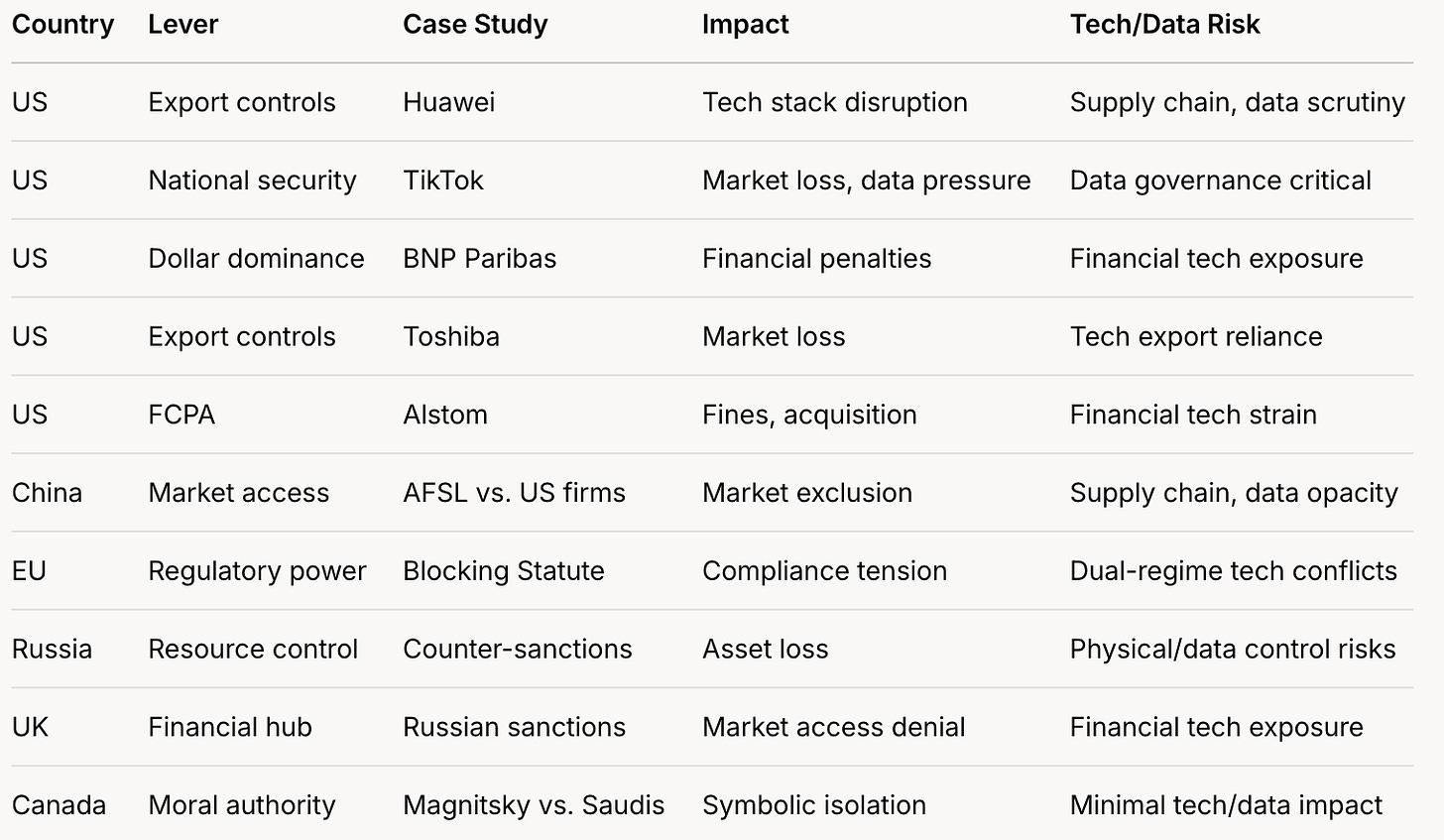
Case Study 1: Huawei (China) - Export Controls
Background: Huawei, a Chinese telecom giant, faced US sanctions starting in 2019 over alleged espionage risks. By 2024, it reported growth despite setbacks, per The Guardian.
Lever Used: Export controls via the Entity List under the Export Administration Regulations (EAR).
How It Was Done: The US Commerce Department’s Bureau of Industry and Security (BIS) restricted US firms from selling technology to Huawei, expanding the Foreign Direct Product Rule in 2020 to block non-US chipmakers using American tech. This targeted Huawei’s tech stack, particularly its reliance on US semiconductors.
Impact: Huawei’s international sales plummeted, forcing a shift to Chinese alternatives, though its 2024 Mate 60 phone showed resilience.
Risks to Tech Stack and Data: Loss of US chips disrupted hardware production; data governance faced scrutiny over alleged Chinese access.
Prevention: Earlier diversification of chip suppliers or transparency on data practices might have softened US actions, though geopolitical tensions limited options.
Preparedness: Invest in R&D for self-sufficiency, diversify supply chains, and monitor US export policies.
Case Study 2: TikTok (ByteDance, China) - National Security Threats
Background: TikTok, owned by ByteDance, faces a potential US ban by January 19, 2025, unless divested, per The New York Times.
Lever Used: National security concerns under the Protecting Americans from Foreign Adversary Controlled Applications Act (PAFACA).
How It Was Done: Congress mandated divestiture or a ban, upheld by the Supreme Court, citing risks of Chinese data access for 170 million US users. App store enforcement amplified pressure.
Impact: ByteDance risks losing its US market or selling TikTok without its algorithm, per Reuters.
Risks to Tech Stack and Data: Data governance is central—US fears of Chinese surveillance threaten operations.
Prevention: Localizing US data (e.g., with Oracle) and separating operations earlier could have mitigated risks - although not for certain since it’s also political.
Preparedness: Localize data storage, enhance transparency, and diversify revenue beyond vulnerable markets.
Case Study 3: BNP Paribas (France) - Sanctions Enforcement
Background: In 2014, BNP Paribas paid a $8.9 billion fine for violating US sanctions, per the DOJ.
Lever Used: The US dollar’s global dominance under the International Emergency Economic Powers Act (IEEPA).
How It Was Done: The DOJ and New York regulators penalized BNP for processing transactions for Sudan, Iran, and Cuba via US banks, threatening its dollar-clearing license.
Impact: Financial and reputational damage, with a temporary clearing suspension.
Risks to Tech Stack and Data: Financial systems reliant on US infrastructure were exposed; data governance was less directly impacted.
Prevention: Stricter sanctions compliance or reduced dollar use might have limited exposure.
Preparedness: Diversify financial systems, train on extraterritorial risks, and explore alternative currencies.
Case Study 4: Toshiba (Japan, 1980s) - Export Controls
Background: Toshiba Machine Co. faced US ire in 1987 for selling milling machines to the USSR, per historical accounts.
Lever Used: Export controls under the Export Administration Act and COCOM agreements.
How It Was Done: The US banned Toshiba imports, costing $2 billion, and pressured Japan to act, targeting its tech exports.
Impact: Financial losses and strained US-Japan ties.
Risks to Tech Stack and Data: Tech stack reliance on US markets was exposed; data governance was not a focus then.
Prevention: Adherence to COCOM or market diversification could have helped.
Preparedness: Align with export regimes, diversify markets, and monitor Cold War-style tech restrictions.
Case Study 5: Alstom (France) - FCPA Prosecution
Background: Alstom paid $772 million in 2014 for bribery under the FCPA, per the DOJ.
Lever Used: The Foreign Corrupt Practices Act’s extraterritorial reach.
How It Was Done: The DOJ charged Alstom for $75 million in global bribes, leveraging its US listing, and pressured its sale to GE.
Impact: Fines, loss of independence, and French claims of economic coercion.
Risks to Tech Stack and Data: Financial penalties hit tech investments; data governance was secondary.
Prevention: Stronger anti-bribery controls or delisting from US exchanges might have reduced risks.
Preparedness: Minimize US jurisdictional hooks, enhance compliance, and prepare legal defenses.
Part 2: Non-US Extraterritorial Actions
Other nations are increasingly mirroring US tactics, using their own levers. Below are five examples.
Case Study 6: China - Anti-Foreign Sanctions Law (AFSL) Against US Firms
Background: China’s AFSL, enacted in 2021, targets entities complying with Western sanctions, per Reuters.
Lever Used: Market access and legal bans.
How It Was Done: China sanctioned US firms like Lockheed Martin in 2023 for Taiwan arms sales, freezing assets and banning market entry.
Impact: Loss of China’s market disrupts supply chains and revenue.
Risks to Tech Stack and Data: Tech firms face exclusion; data governance risks rise with China’s opaque enforcement.
Prevention: Reducing China exposure or lobbying for de-escalation could help.
Preparedness: Diversify markets, assess China risks, and clarify compliance with Beijing.
Case Study 7: EU - Blocking Statute Against US Sanctions
Background: The EU’s Blocking Statute counters US sanctions, updated in 2018, per the European External Action Service.
Lever Used: Regulatory authority over the single market.
How It Was Done: The EU barred compliance with US Iran sanctions, with a 2021 German ruling favoring Bank Melli Iran. INSTEX facilitated trade.
Impact: Limited success due to US market pull.
Risks to Tech Stack and Data: Firms navigating dual regimes face tech and data compliance conflicts.
Prevention: US firms could seek EU exemptions, though unlikely.
Preparedness: Align with EU laws, explore non-dollar trade, and leverage EU diplomacy.
Case Study 8: Russia - Counter-Sanctions Against Western Firms
Background: Russia retaliated post-2014 Crimea sanctions, per BBC.
Lever Used: Resource control and asset seizures.
How It Was Done: Russia banned EU/US agricultural imports and seized assets of exiting firms like McDonald’s in 2022.
Impact: Western firms lost billions and assets.
Risks to Tech Stack and Data: Physical asset loss; data risks from Russian control.
Prevention: Neutral operations or early exits might have mitigated losses.
Preparedness: Diversify from Russia, secure assets legally, and monitor policies.
Case Study 9: UK - Sanctions on Russian Entities
Background: Post-Brexit, the UK targeted Russian firms like Evraz in 2022, per the UK Government.
Lever Used: Financial hub status under the Sanctions and Anti-Money Laundering Act 2018.
How It Was Done: The Office of Financial Sanctions Implementation froze assets and banned transactions linked to oligarchs.
Impact: Loss of London market access, though global reach is limited.
Risks to Tech Stack and Data: Financial exposure; data less directly affected.
Prevention: Reducing UK ties or diplomatic efforts might have helped.
Preparedness: Minimize UK financial footprints and comply locally.
Case Study 10: Canada - Magnitsky Sanctions on Saudi Officials
Background: Canada sanctioned 17 Saudis in 2018 over Khashoggi’s murder, per Global Affairs Canada.
Lever Used: Moral authority under the Justice for Victims of Corrupt Foreign Officials Act.
How It Was Done: Asset freezes and entry bans via Canadian banks.
Impact: Symbolic pressure with modest global effect.
Risks to Tech Stack and Data: Minimal direct tech impact; data risks low.
Prevention: Avoiding Canadian jurisdiction or addressing rights issues could reduce risks.
Preparedness: Avoid Canadian touchpoints and monitor rights scrutiny.
Part 3: Comparative Analysis and Corporate Implications
Comparative Table
Learnings for Tech & Business Leaders
Your company is likely exposed to U.S. legal jurisdiction in more ways than you think — through:
Cloud vendors (AWS, Azure, GCP)
Digital payments (Stripe, Visa, Mastercard)
Software dependencies and licensing
USD-based invoices and banking contracts
IP registration and global enforcement channels
This affects your:
Compliance obligations
Data sovereignty posture
Resilience in geopolitically sensitive regions
Roadmap for Managing Legal and Geopolitical Exposure in Your Tech and Data Stack
In a multipolar world where legal jurisdictions travel through code, contracts, and cloud, global business leaders must shift from compliance by default to sovereignty by design.
This roadmap offers a step-by-step guide to help corporate leaders identify, classify, prioritize, and mitigate risks linked to the extraterritorial reach of dominant powers like the United States, China, and the EU.
Phase 1: Identify and Map Your Exposure
Start with a forensic audit across your organization’s infrastructure, financial flows, and regulatory obligations.
Checklist:
Monetary Flows: Where are you using USD in invoices, payment gateways, SWIFT transactions, or intercompany financing?
Cloud & SaaS Stack: Which vendors are U.S.-based or store data on U.S.-controlled infrastructure (AWS, Azure, GCP)?
Software Dependencies: Are you relying on tools or licensing governed by U.S. export controls (e.g., encryption, semiconductors)?
IP and Legal Presence: Are you listed on U.S. exchanges or filing patents with U.S. regulators?
👉 Tip: Integrate this audit into your enterprise risk management (ERM) and cross-border compliance reviews.
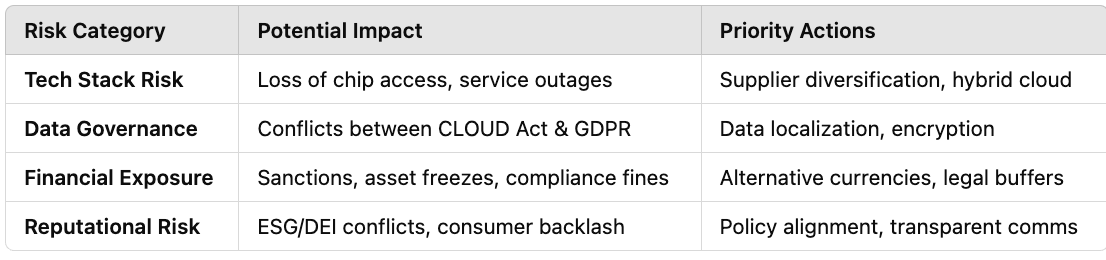
Phase 2: Classify and Prioritize Risks
Once exposure is mapped, sort them into strategic buckets by type and severity.
👉 Tip: Apply a “heat map” approach — classify risks by probability and business impact.
Phase 3: Diversify Core Infrastructure and Legal Dependencies
Infrastructure Resilience
Shift toward multi-cloud or sovereign cloud strategies using EU or APAC vendors.
Develop on-prem or hybrid architectures for mission-critical systems (especially in AI, defense, finance).
Track BIS Entity List to anticipate supply chain sanctions.
Financial Operations
Where feasible, test non-USD settlement pilots (e.g., using EUR, RMB, or local currency in MENA/ASEAN).
Reevaluate exposure to U.S.-based payment rails (Visa, Stripe, PayPal).
Data Governance
Localize sensitive data within legal jurisdictions aligned with your operational footprint.
Deploy geo-fencing, encryption, and access management to reduce seizure risk.
Reference: CSIS TikTok & National Security
Phase 4: Scenario Planning and Simulation
Model Key Disruption Scenarios:
Sudden loss of access to U.S. cloud or chips (Huawei playbook)
SWIFT disconnection (BNP Paribas precedent)
Regulatory conflict between U.S. sanctions and EU GDPR
Build Contingencies:
Secondary cloud stack and payment rails
Supply chain rerouting pathways
Alternate entity structures for dual-market compliance
👉 Tip: Include these in board-level business continuity and geopolitical risk workshops.
Phase 5: Proactive Policy Engagement
Engage Strategically With:
WTO reform initiatives (cross-border data flow frameworks)
Digital trade treaties (DEPA, OECD, ASEAN frameworks)
National governments on IP, cloud, and data residency norms
Join or Initiate:
Industry coalitions advocating for multilateral legal harmonization
Global working groups on cross-border digital trust and open standards
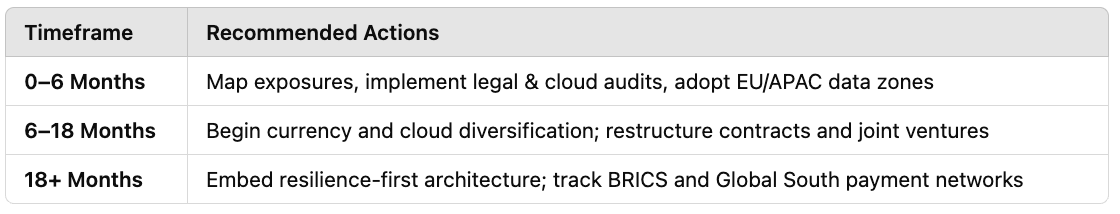
Timeline and Implementation Phases
Sovereignty Is Strategy
In the 2025 landscape, legal jurisdiction is embedded in infrastructure choices. Whether through your payment processor, your cloud provider, or your chip supplier — you're making geopolitical decisions every day.
To grow responsibly and competitively in this environment, corporate leaders must think beyond ROI and uptime. They must build infrastructure that resists legal overreach, systems that enable digital sovereignty, and policies that prioritize resilience over convenience.
Further Reading & Tools:
Going Forward: Risk-Aware Growth in a Multipolar Order
The new global economic order is not about retreat — it's about calculated diversification and systemic resilience.
Digital sovereignty, multi-jurisdictional compliance, and payment flexibility are becoming as important as scale and uptime.
The question isn't whether the U.S. dollar still dominates — it does.
The real question is whether your enterprise is overexposed to a single geopolitical regime.
Leaders who want to stay competitive must:
Plan beyond convenience
Build with neutrality in mind
Design operations for legal and infrastructural agility
Conclusion: Build for Resilience, Not Convenience
Global businesses no longer have the luxury of passive neutrality. If your systems, contracts, or data flow through the U.S., you are already bound by its laws and risks — whether you intended to be or not.
The time to audit, diversify, and de-risk is now.
Because in this new multipolar world, control isn’t always about code — it’s about currency.
Explore More from KoncentriK
Questions? Comments? Drop me a note at damien.kopp@rebootup.com or :
thanks for reading!
Damien